
edit: 12th of March; Follow-up availible; Click Here
In this howto, I will show you some things I have done to secure OS X beyond its default settings. There are very basic, and some advanced things in here. I am in NO WAY LIABLE for ANY DAMAGE you might do to your Mac by messing around with the things I describe here, because it could very easily cut you off from the internet if you don’t know what you are doing, and you’ll be emailing me to death from some internet café while receiving strange looks from people because you just ate your Mac’s supplied stickers.
First off, there is some odd stuff going on with Tiger’s default security settings. Upon setting up your Mac, you are essentially it’s administrator. You can even change the password of the highest power on the computer, root. Therefore, if there ever would be a security danger, and you are running with such privileges, it is a lot easier to exploit the system. To fix this hassle, make a new user. Awww, you just had your whole Mac set up with a ton of programs and settings? What, you are expecting me for some migratory script? Well, suck it up, because it’s not done yet. Swallow the bitter pill for now, as I am still struggling with the ‘defaults’ command-line tool to copy all the settings. You can relieve some loss of settings by copying relevant preferences from (Initial User)/Library/Preferences to (New User)/Library/Preferences. NOTE: NOT /Library! The Library folder in your $HOME. (EDIT; gregr over at digg pointed this out: “- if you have your account set up the way you want, then create a new user as advised here but make that the admin one (just don’t call it admin or similar), put a good password on it and then make your user a ‘normal’ user.” This is, of course, a much more hassle-free way to do this. Thanks gregr!
Also, people rarely realize – your firewall is off by default. Even better, we have an intensely impressive firewall option. First, here’s the gem; it’s hidden in the Sharing preference pane (what genius thought that one up?) under it’s own tab. And there, the fun begins.
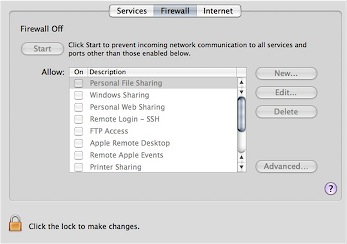
What is all this then? Oh, remember, you created a new, unprivileged account. Just checking on you.
Ok, unlock the thing, authenticate, and click the obvious ‘Start’ button. It’s on when it reads stop. Easy so far. Now, click the almost hidden “Advanced” button.
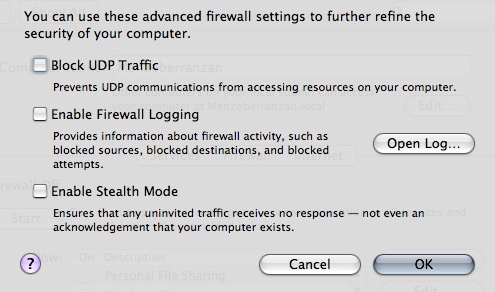
Ooh, doesn’t that sound yummy. “Stealth Mode”? Damn, screw all that, my Mac’s going to be like a fucking Stealth Plane! Uh, anyway, ignore the buzz for now and check it out; UDP filtering is off by default, this ‘Stealth mode’ thing is off, and logging too. Insane. Put them all on. Little note here; if you want to be a diehard bittorrent downloader and want to optimize other P2P traffic, you best leave the UDP filtering out. What does this leave for attackers? Network Time, 2 exploits in the last years, CUPS (Printing), 1 DoS exploit found and strangely, MS Word (use OpenOffice.org!).
So, does this all do what it says? Nope. If you don’t want to share your printer, or share files over the Windows protocol, then these are left open, regardless of what you fiddle with in the preference panels. Bonjour is also always allowed in, and for some arcane reason, DNS is allowed outwards. This is almost like waiting for an exploit to happen. To somewhat augment these insane defaults, you can open a terminal and fiddle around with the ipfw command. You will need priviledges, gained by using sudo. You can also use Waterroof, a visual editor of your firewall rules. Dandy.
Anyway, the UDP filtering by default just allows anything Bonjour and Printing Server in. To fix this strange behaviour, just use ipfw;
sudo ipfw del 20321 followed by;
ipfw del 20322
Only do this with all settings in the ‘Advanced’ tab enabled! You might end up deleting the wrong firewall records. Anyway, what does this do to secure you? With inbound Bonjour UDP and CUPS UDP forbidden, foreign hosts will not be able to see what patchlevel you have (OS Version and Hardware type) and not be able to use CUPS exploits. It disables printer sharing, iTunes sharing, and other Bonjour-services.
Now, the Firewall a bit more secure, you can check to make sure Bluetooth is off by default (it is ON and discoverable on new users by default), and that it is set to non-discoverable. Now, click the Bluetooth icon in the menu bar, and go to Bluetooth Preferences.
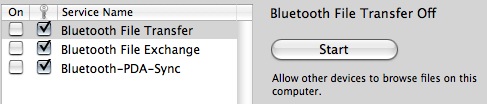
Ensure that the checkmarks are like in the picture. Most important here is the field with the key icon, which means authentication is on. Some are off by default, an insanely stupid move. There are lots and lots of Bluetooth vulnerabilities out there, and the first worm for OS X used Bluetooth to propagate itself.
Other common security fixes for everyday life is ensuring you log into gmail with https://, and browse Gmail with https://. Gmail drops the secure session after login, but you can force it by typing https://gmail… in the browser. In Apple Mail, make sure you have encryption enabled. Otherwise, you can secure a non-secure connection to a server you have SSH access to with the following terminal command;
sudo ssh2 -l username@server.com -L 25:server.com:25 -L 110:server.com:110 server.com
This essentially forwards the ports 25, and 110 (respectively SMTP and POP3, replace for IMAP or IMAPS with adequate port numbers) to the server in question and ‘tunnels’ the traffic through SSH, encrypted et al. You can now set the server settings in Mail for incoming to ‘localhost:110’ (without the brackets, doh) and outgoing to ‘localhost:25’. The ssh2 command forces SSH2.0, for more security.
For Laptop safety, you can first disable the most stupid feature in history, namely auto-login. It will make it much easier for people who steal your laptop to make use of it. This included people with sensitive data, who, if they don’t mind performance degradation, should use my settings;
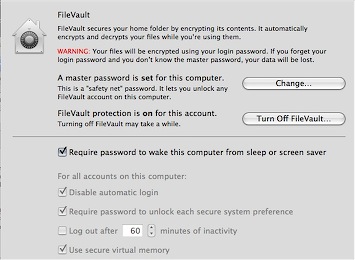
Yup, disable auto-login, make sure there is a pass on your screen saver / wake-up, ensure virtual memory is encrypted (performance drop here) and Filevault is on with a very complex password that stretches the imagination. (and don’t start asking me why this is greyed out)
Okay, so that all makes us a bit more secure and aware of our security. For other security, in the sense of anonymous internet access, you can use Vidalia with Tor. There was a recent proof-of-concept attack on Tor, but it’s not to be used as a completely anonymizing tool – it does it’s work very well, though, and it goes recommended for any computer for me.
This concludes this howto to harden OS X. If you have the abilities to compile something, please take a look at Bastille for OS X, whose co-author Jay Beale showed many of the faults in defaults in this document. It requires X11, the developer tools, and the latest developer release of Perl-Tk to function, and it can assess your system security with a number. It will automate many of the things I have advised and howto’d here in a friendly Tk-dialog. For now, have fun hardening your OS, and remember, hardening breaks future exploits! With the surge in Apple’s marketshare, we will start seeing malware.
Since this article got dugg, I have gotten a lot of feedback. Don’t miss these useful tips from readers;
– There is an often overlooked feature in Safari’s preferences to disable the automatic opening of disk images. This feature has had many exploits since it’s advent (contributed on digg by newbill123.
– For the truly paranoid, set the Firmware Password with the tool in your /Applications/Utilities folder to ensure no CD is bootable or the settings immutable without a password (contributed on digg by the ‘friendly’ frozendice).
– I will touch on more hints, tips, and hardening documents in the next how-to.



meta_serif.gif)


